By Jeff White (karttoon)
I've been continuing to work on tracking the MAN1 group's deployment of Hancitor/H1N1 documents and have analzyed/ran all samples I have access to for August/September (37,283) through my decryptor, along with a handful of additional scripts, to build a massive file of meta-data and IoC's. I wanted to release it to the public so I've put it on $dayjob's GitHub.
The main CSV fields map to the below:
"sha256","P2","P3","P3PAY","P1","P1HEAD","P4","P1ADD","P1XOR","P2FILEVER","P3URLS","P1SIZE","P2FILEDESC","P4PAY","P1MAGIC","P2COMPNAME","DATE","P1ORIGNAME","P2PRODNAME","P1COMPNAME","YARA","P1FILEDESC","P3XOR","P1INTNAME","P4URLS","P1COPY","P2INTNAME","P1B64","P1URLS","P1PRODNAME","P2URLS","P1PAY","P2XOR","P1FILEVER","P2COPY","P2ORIGNAME",”P2PAY"
For the most part the fields correlate to the various stages of my decryptor. The PE related meta-fields are extracted from the embedded payloads once I've ripped them out.
Below are a few excerpts of the data...
hxxp://21naillounge.com/wp-includes/Requests/Exception/Transport/ls.exe
hxxp://andmabi.com/ls/gate.php
hxxp://andrutoffa.com/ls4/gate.php
hxxp://arrysiet.ru/ls5/gate.php
hxxp://atsinrobevent.ru/ls4/gate.php
hxxp://bettitotuld.com/ls3/gate.php
hxxp://bongants.com/wp-content/themes/sketch/tmp.exe
hxxp://bureugut.ru/ls5/gate.php
hxxp://busofketper.com/ls4/gate.php
hxxp://callereb.com/ls/gate.php
hxxp://cediac.mobi/wp-content/plugins/diacce-albums-plugin/images/ls.exe
hxxp://covemotert.ru/ls4/gate.php
hxxp://dafiutrat.ru/ls3/gate.php
hxxp://dingtalhedtuse.com/ls4/gate.php
hxxp://evengwafiot.ru/h/gate.php
hxxp://eventhedtsiar.com/ls5/gate.php
hxxp://eventtorshendint.ru/ls3/gate.php
hxxp://fehisresro.com/ls5/gate.php
hxxp://fejusttold.ru/ls/gate.php
hxxp://fofaarty.ru/ls5/gate.php
hxxp://gamefoheck.ru/ls5/gate.php
hxxp://gewilaningrec.ru/ls4/gate.php
hxxp://goldencaribootours.com/modules/mod_superfishmenu/tmpl/js/ls.exe
hxxp://hecksafaor.com/h/gate.php
hxxp://helahatun.com/ls3/gate.php
hxxp://henenverfort.ru/ls4/gate.php
hxxp://hersmabeand.com/ls5/gate.php
hxxp://hinhenharre.ru/ls3/gate.php
hxxp://hinromfor.com/ls/gate.php
hxxp://howrighhehat.ru/ls/gate.php
hxxp://idmuchatbut.ru/ls3/gate.php
hxxp://joeventinve.ru/h/gate.php
hxxp://johnhowkette.com/ls5/gate.php
hxxp://johntotrepwron.com/ls4/gate.php
hxxp://kinperileft.ru/h/gate.php
hxxp://kinperileft.ru/ls4/gate.php
hxxp://lacninghanar.com/ls/gate.php
hxxp://latotrepma.ru/ls4/gate.php
hxxp://mianingrabted.ru/h/gate.php
hxxp://michanic.ru/lbozjd/shabs/tmp.exe
hxxp://muchidonhen.ru/ls5/gate.php
hxxp://mywassnoaning.ru/ls/gate.php
hxxp://noruromin.com/ls3/gate.php
hxxp://onehepherthin.ru/h/gate.php
hxxp://onehepherthin.ru/ls6/gate.php
hxxp://onketorsco.com/ls3/gate.php
hxxp://opweb.xyz/modules/mod_ariimageslidersa/tmp.exe
hxxp://otinrofha.ru/ls4/gate.php
hxxp://perunkehem.ru/ls4/gate.php
hxxp://prettynailsfl.com/profiles/testing/modules/drupal_system_listing_incompatible_test/ls.exe
hxxp://qualyandco.com/wp-content/themes/qualy-co/tmp.exe
hxxp://rantertinhe.ru/h/gate.php
hxxp://redidfe.ru/ls/gate.php
hxxp://resrebsedrol.ru/ls4/gate.php
hxxp://rinwasceand.ru/ls4/gate.php
hxxp://ritbotohem.ru/h/gate.php
hxxp://ritbotohem.ru/ls4/gate.php
hxxp://robinfortfa.com/h/gate.php
hxxp://romarbe.ru/ls/gate.php
hxxp://romorlittbet.com/ls4/gate.php
hxxp://roprinromrow.ru/ls3/gate.php
hxxp://rusinhoun.ru/ls5/gate.php
hxxp://saherresot.ru/ls5/gate.php
hxxp://sandrikedot.ru/ls5/gate.php
hxxp://sarowrebted.ru/h/gate.php
hxxp://shaheenoman.com/plugins/editors/tinymce/fields/ls.exe
hxxp://sincyhespar.ru/ls5/gate.php
hxxp://sinsedmuchor.com/ls4/gate.php
hxxp://sohenlega.ru/h/gate.php
hxxp://sohenlega.ru/ls6/gate.php
hxxp://sonotsandthat.ru/ls4/gate.php
hxxp://sorolgoteveng.com/h/gate.php
hxxp://supketwron.ru/ls/gate.php
hxxp://tafajohnet.ru/ls4/gate.php
hxxp://tefaverrol.ru/ls3/gate.php
hxxp://thehentoftbet.ru/ls4/gate.php
hxxp://thetrocotof.ru/ls4/gate.php
hxxp://tingapeper.ru/ls5/gate.php
hxxp://tonslacsotont.ru/ls3/gate.php
hxxp://torinverwa.ru/h/gate.php
hxxp://torsketronand.ru/ls4/gate.php
hxxp://totrovefort.ru/ls4/gate.php
hxxp://totwoveret.com/ls4/gate.php
hxxp://tyatmorow.com/ls6/gate.php
hxxp://ughlittrinthe.ru/ls3/gate.php
hxxp://ughtontrofhe.com/ls5/gate.php
hxxp://undwohed.ru/ls/gate.php
hxxp://utthettorssed.com/ls4/gate.php
hxxp://vetomoof.ru/h/gate.php
hxxp://wassrefrightons.ru/h/gate.php
hxxp://wilthetedot.com/h/gate.php
hxxp://wilthetedot.com/ls4/gate.php
hxxp://witjono.ru/ls/gate.php
hxxp://witruterred.ru/ls4/gate.php
hxxp://wotalhedron.com/h/gate.php
hxxp://www.sacacademy.com/images/design/prettyPhoto/dark_rounded/tmp.exe
A large chunk of the registered domains correlate back to Marek (who has been blogged about previously).
Name | Email | Country | State | City | Street | Telephone | Organization
Marek Kazuewsky | marekkazuewsky@gazeta.pl | poland | mazowieckie | warszawa | Tamka str, 6 fl 41 | 3513129795033 | NA
The company names in the PE meta showed a pretty clear pattern as well. The number proceeding the name are the number of samples that had it.
27097 SynapticosSoft, Corporation.
1502 SynSoft, Corporation.
1478 BonsSofts
677 Synaptoft, Corporation.
365 Syft, Corporation.
362 SySoft, Corporation.
307 *FontsSofts
192 SicosSoft, Corporation.
106 &BonsSoft
69 SycosSoft, Corporation.
60 SynicoSoft, Corporation.
50 BonsSoft
36 SynaosSoft, Corporation.
32 SynosSoft, Corporation.
31 SosSoft, Corporation.
28 SynapsSoft, Corporation.
26 *BonsSofts
19 SynticSoft, Corporation.
19 SynaptisSoft, Corporation.
19 SynacosSoft, Corporation.
19 SynaSoft, Corporation.
19 FontsSofts
18 SynasSoft, Corporation.
17 SypticSoft, Corporation.
12 OlieSoftWare
11 SynapcosSoft, Corporation.
10 SynaptsSoft, Corporation.
9 ^VolSoft
8 SyssesSoft, Corporation.
8 SynicSoft, Corporation.
8 SyicosSoft, Corporation.
7 SynaposSoft, Corporation.
6 Synoft, Corporation.
6 SoftMarket
6 &VolSoft&
6 VolSoft.
5 Synapqoft, Corporation.
5 %VolSoft
3 GolSoft
2 ^GolSoft
1 SynicosSoft, Corporation.
1 Synapoft, Corporation.
1 QQQ&AlinSoft
1 HHH&AlinSoft
Example tracking campaigns by XOR keys in the 2nd stage with this data.
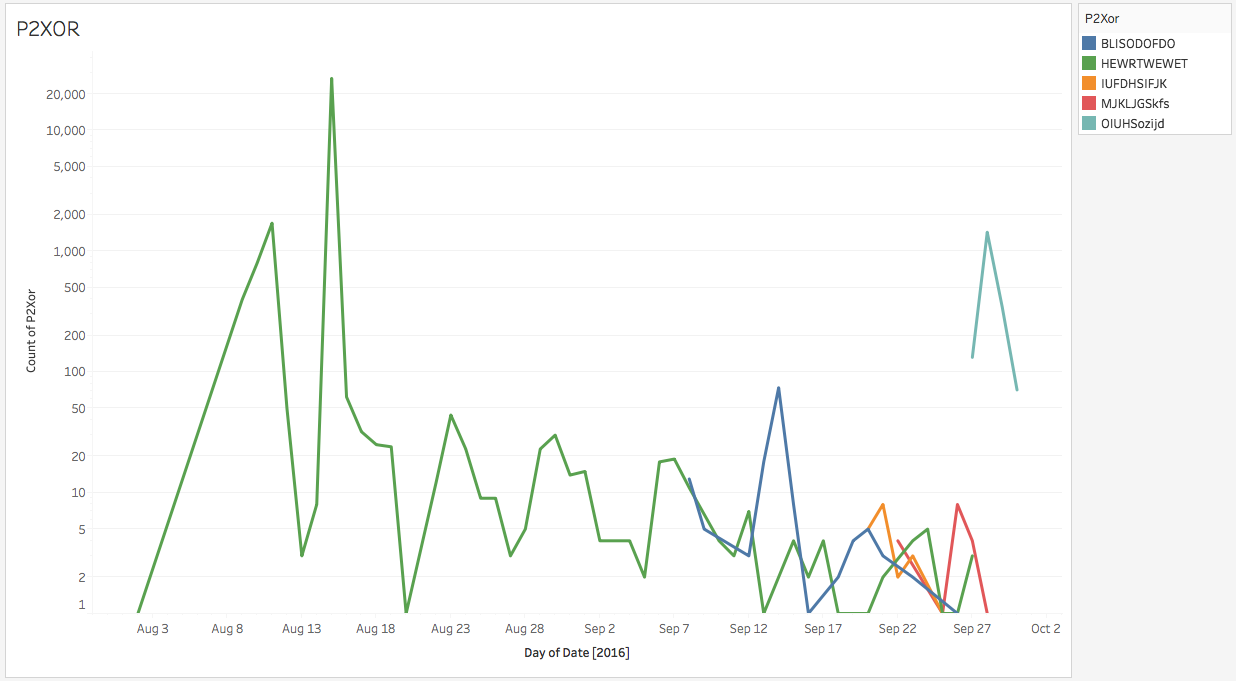
Another example using the data to track when the MAN1 group has shifted their API calls in the Microsoft Word Documents.
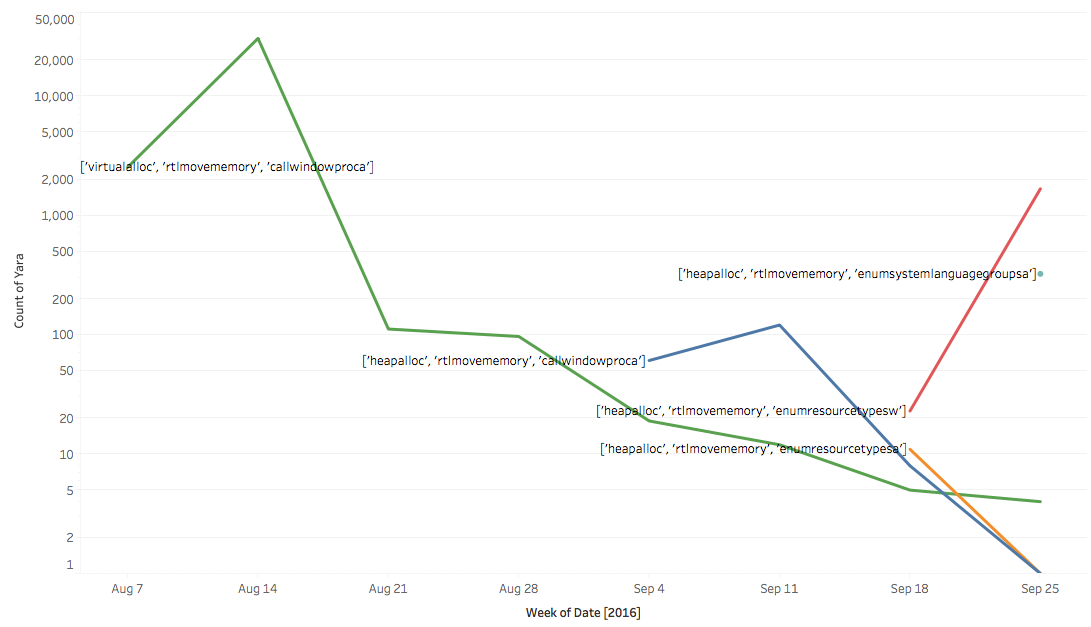
If the research proves useful to you, or you need clarification, just drop me a line.
Older posts...

